In lots of massive firms, the principal reason behind deploying Network Access Control (NAC) is to protect versus access to The inner community. NAC devices make the workers validate their tools In order to determine community connections only with accredited equipment. As an example, a company may commit to use NAC so as to apply stability insurance policies for example The newest variations of antivirus and up to date working methods among Many others.
seven. Remotely accessing an employer’s inside community utilizing a VPN Smartphones can even be secured with access controls that enable just the user to open the product.
Tightly built-in product suite that allows security teams of any size to rapidly detect, look into and reply to threats over the company.
DevSecOps incorporates stability in the DevOps approach. Discover the best way to carry out security tactics seamlessly in your development lifecycle.
DAC is the easiest and most versatile style of access control product to operate with. In DAC, the operator with the source routines his privilege to permit others access to his resources. But the spontaneity in granting this authorization has flexibilities, and concurrently results in a safety hazard In the event the get more info permissions are dealt with injudiciously.
e., transmitting several streams of knowledge between two conclude factors concurrently which have founded a connection in network. It is usually
That functionality executed with the useful resource controller that allocates system assets to fulfill user requests.
Help and servicing: Go with a Resource which has reputable assist and that often supplies updates in order to take care of emergent protection threats.
This makes access control essential to making sure that sensitive knowledge, as well as critical techniques, remains guarded from unauthorized access which could lead to a knowledge breach and result in the destruction of its integrity or trustworthiness. Singularity’s System presents AI-pushed security to make sure access is adequately managed and enforced.
six. Rule-based access control A rule-based method sees a program admin outline policies that govern access to company methods. These regulations are generally crafted around conditions, like the location or time of working day that people access methods. What exactly are Some Approaches For Applying Access Control? Among the most prevalent procedures for applying access controls is to utilize VPNs.
Rule-based access control: A stability design where an administrator defines procedures that govern access on the resource.
Rather than control permissions manually, most stability-pushed organizations lean on identification and access administration solutions to employ access control insurance policies.
Implementing the correct access control technique customized to your preferences can noticeably enhance security, streamline operations, and provide assurance.
Listed here, the system checks the user’s identification against predefined guidelines of access and will allow or denies access to a specific source dependant on the user’s position and permissions related to the part attributed to that consumer.
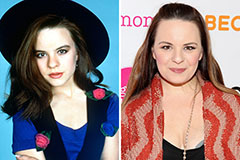 Jenna Von Oy Then & Now!
Jenna Von Oy Then & Now! Jeremy Miller Then & Now!
Jeremy Miller Then & Now! Susan Dey Then & Now!
Susan Dey Then & Now! Heather Locklear Then & Now!
Heather Locklear Then & Now! Jane Carrey Then & Now!
Jane Carrey Then & Now!